Security Operations Center (SOC)-as-a-Service
As virtually all SMBs lack security teams that are available 24x7, these companies need to turn somewhere to receive continuous security monitoring services necessary to timely identify and take action on potential cybersecurity threats. This capability is also necessary to satisfy cyber insurance requirements, and depending on the industry you operate in, to satisfy regulatory requirements.
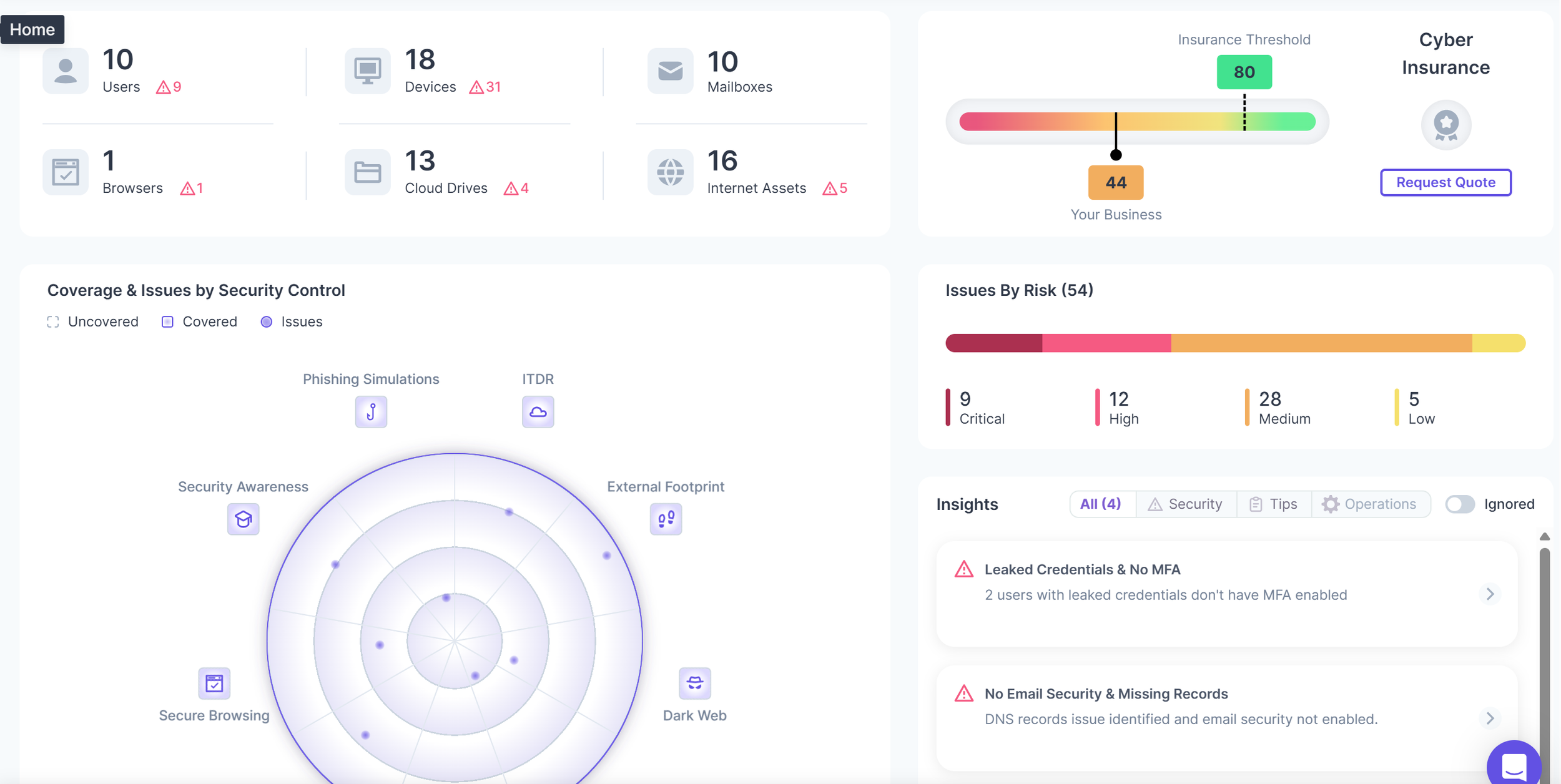
Through our SOC-as-a-Service offering, we help our clients meet these requirements through the use of our automated, AI-powered monitoring platform - SafeHaven.
SafeHaven is available to our clients for a flat, monthly rate that is driven by the number of users in your environment and the number of devices which require monitoring. As part of this rate, you also receive the expertise provided by the cybersecurity experts at Malcom Risk Advisors to help you remediate any potential security incidents upon identification.
This transparent, affordable costing model makes SafeHaven a ‘must have’ security capability for all SMBs - providing you with the same cybersecurity protection capabilities utilized by enterprise organizations, at a fraction of the cost.
Utilizing a set of cybersecurity controls and capabilities that are most critical when it comes to identifying cyberattacks on your network, the SafeHaven platform provides our clients with around-the-clock protection from cyber threats by:
24x7 Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR) capabilities provided via our partners at SentinelOne or CrowdStrike.
Identification of areas within your network that do not require multi-factor authentication (MFA) in order to access system resources.
AI-driven auditing and logging capabilities which analyze end user activity for anomalous behavior, identifying potential cyber threats before they can be exploited by cyber criminal and impact your organization’s business operations.
Regularly scheduled vulnerability and configuration scanning of your network and cloud environments to ensure your infrastructure is protected by the most recently released security patches and software updates, and that environments aren’t erroneously configured, thus allowing your data stored in the cloud available to be available to the public.
Email security tools that quarantine messages with a high likelihood of being spam or a phishing email, preventing them from ever reaching your end users.
Secure browser extensions that protect your end users from accessing malicious websites and links when using the internet.
Identification of stale end user accounts that have not been utilized for an extended period of time, representing potential unnecessary user access.